Sharemind MPC
Components
Sharemind MPC deployment consists of two types of components – application servers and client applications. Sharemind Application Server implements the MPC computation node role, it talks to other Application Servers during MPC protocols and to client applications for user input and output. It also has a local persistent storage for saving input shares and computation results between computations. For example, a typical Sharemind MPC deployment supporting the shared3p protection domain has three application servers and any number of client applications.
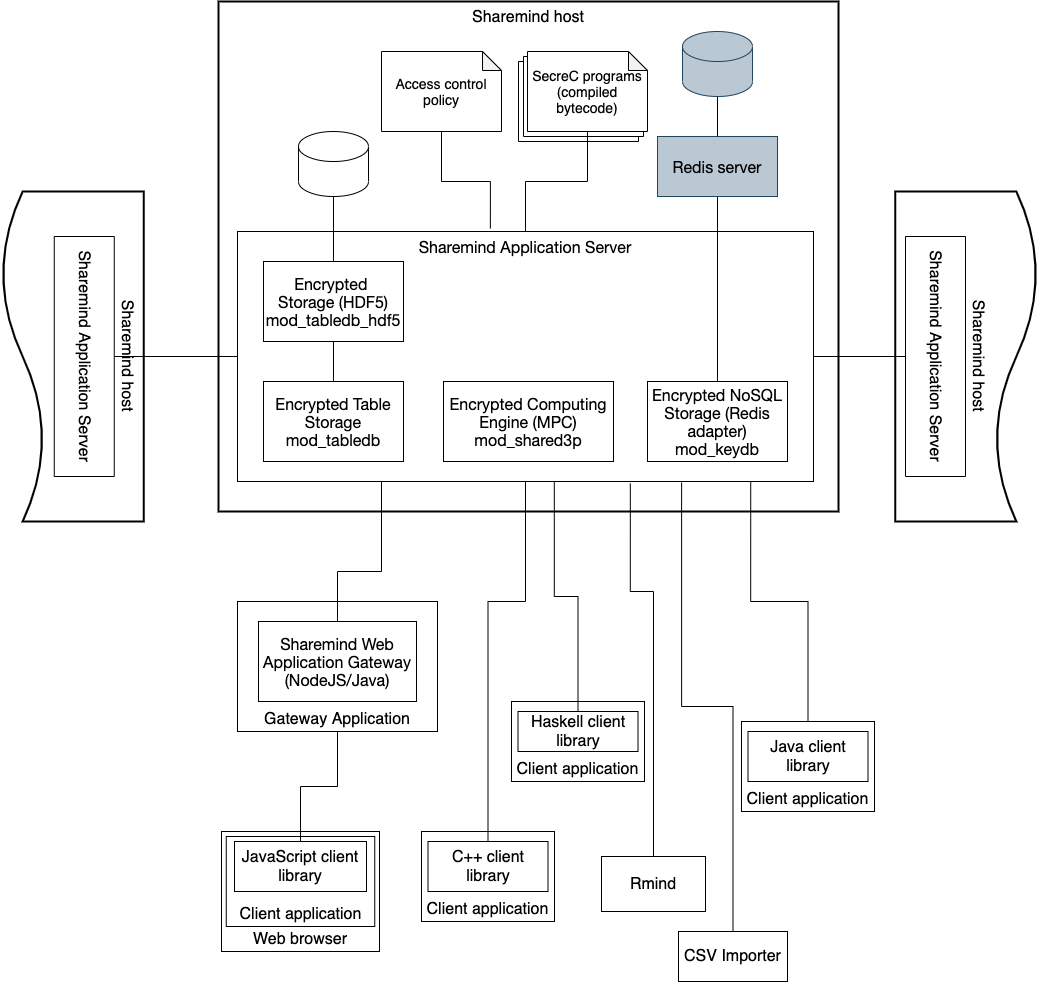
Application Server modules
Encrypted Computing Engine (mod_shared3p)
Encrypted Computing Engine is an application server and a core component of the Sharemind platform that facilitates running secure multi-party computation programs. These programs are written in the SecreC language that separates public and encrypted data work flows.
Sharemind Encrypted Computing Engine implements secure computation protocols based on 3-party additive secret sharing. Therefore, a Sharemind deployment consists of three parties, each hosting their own Encrypted Computing Engine.
Encrypted Storage (Embedded HDF5, mod_tabledb_hdf5)
The Encrypted Storage (Embedded HDF5) provides a persistent storage layer for the Sharemind Application Servers (Encrypted Computing Engine and Emulator). It is used to store input values and computation results, both of which may be either public or encrypted.
The Encrypted Storage add-on is based on HDF5 technology, which provides an efficient column-optimised storage of high volume data.
Encrypted NoSQL Storage (Redis adapter, mod_keydb)
The Encrypted NoSQL Storage (Redis adapter) provides a persistent storage layer for the Sharemind Application Servers (Encrypted Computing Engine and Emulator). It is used to store input values and computation results, both of which may be either public or encrypted.
This add-on provides an efficient key-value interface for data storage. It requires a Redis backend at each Sharemind Application Server host.
Sharemind Web Gateway
Sharemind Web Gateway (SWG) provides a HTTP/HTTPS interface for your Sharemind Encrypted Computing Engine, so you can build privacy-preserving web applications, where data is encrypted in end user’s browser.
Each of the three Encrypted Computing Engines needs its own Sharemind Web Gateway that may be deployed at the same host computer. The SWG may also handle application-specific business logic, e.g. cache input shares and starting a secure computing periodically on larger batches of input values. Sharemind Web Gateway functionality is provided through NodeJS and Java libraries.
Encrypted Computing Emulator
Encrypted Computing Emulator provides the same user experience as Sharemind Encrypted Computing Engine, but emulates the secure computing locally without the network communication overhead. Encrypted Computing Emulator is used for developing and testing SecreC programs before deploying them on Encrypted Computing Engine.
Encrypted Computing Emulator provides performance models for secure multi-party computation protocols, so you can evaluate the running time breakdown of you SecreC programs even before deploying them on real installation.
There are two ways to run Encrypted Computing Emulator. First, there is
the stand-alone Sharemind MPC Emulator program that forms the basis of
the Sharemind public SDK. Currently,
this Emulator has no client interface which means that it cannot be used
with command-line or web-based client applications. Instead, the SecreC
bytecode is given directly to the Emulator. Alternatively, the Sharemind
Application Server can be configured with the mod_shared3p_emu module,
keeping all the other features of the Application Server. For example,
you are able to run existing client applications unmodified, by
switching to the cmod_passthrough module in the client configuration.
Client software
Rmind
Rmind is a statistical analysis suite that works on encrypted data. Rmind supports a wide variety of data manipulation and statistical functionality, including descriptive statistics, merging (joining) data tables, aggregations, statistical models as well as visualisations. Analyst will only see statistical aggregate results, while all individual values and intermediary results will stay encrypted on the Sharemind Application Server. People who have previous experience with the R language and tools can appreciate the familiarity of Rmind data mining software.
CSV Importer
The CSV Importer imports a CSV formatted database or Excel spreadsheet export into a Sharemind installation. CSV Importer validates input file according to a given data model description, secret shares each individual value in the CSV input file and distributes the shares among the Sharemind Application Servers in a given installation. CSV Importer is the last step, where sensitive values are available in plaintext, and therefore the tool should be used by Data Owner.
CSV Importer supports comma-, semicolon-, tab- and space-separated input files and various data types, including automatic generation of enumeration types.
Client API
Sharemind Client API provides the necessary tools for building custom client application for the Sharemind platform and integrating secure computation technology into existing information systems.
The Client API consists of libraries, header files and documentation for building and integrating privacy-preserving applications in C, C++, Java, Haskell and JavaScript (to be used with Sharemind Web Gateway).
Running privacy-preserving applications
On Sharemind MPC platform, privacy-preserving applications are developed using the open source SecreC programming language. SecreC is a domain specific language that separates private and public data flows. By marking user’s (and other sensitive) input as private, an application developer can be confident that all computations involving these values are executed in the secure MPC environment. At the same time, the developer does not have to know the underlying MPC protocol details.
An example SecreC program, counting the number of occurrences of a secret value in a vector of secret values:
import shared3p;
import stdlib;
// All variables prefixed with `pd_shared3p` are secret-shared
domain pd_shared3p shared3p;
void main() {
pd_shared3p uint64[[1]] haystack = {1, 2, 3, 4, 5, 6, 7, 8, 9, 10};
// In reality, this comes from database:
// pd_shared3p uint64[[1]] haystack = loadFromDB(...);
pd_shared3p uint64 needle = 5;
// In reality, this comes from user-supplied argument, for example:
// pd_shared3p uint64 needle = argument("needle");
// Because of private operands, the equality operation
// invokes a corresponding MPC protocol
pd_shared3p bool[[1]] match = (needle == haystack);
// Publish orders each computation node to send its
// corresponding share back to the client application
publish("count", sum(match));
}SecreC programs are deployed on Application Servers and invoked by authorised client applications by their name (think of remote procedure calls or stored procedures in database management systems). This happens in parallel in all three Application Servers.
In Sharemind MPC, each Application Server is independent in validating the user query against its access control list (ACL) and the data usage policy.
It is important to notice that each Application Server is independent in deciding a) whether the user is authorised to run a given SecreC program; and b) if the requested SecreC program correctly implements the data usage policy. An MPC protocol cannot be executed if the Application Servers do not reach consensus in these questions. Consequently, a user can only run a predetermined set of programs and a single server or a pair of servers cannot allow potentially malicious queries without the consent of the third server. This provides cryptographic enforcement of data usage policies.
Requirements and Privacy Guarantees
Deploying Sharemind MPC in practice requires that the three Application Servers (computation nodes) are hosted by independent parties who do not collude. Good candidates are government organisations from different jurisdictions or peers that are themselves interested in the correct outcome of the computation.
With the non-collusion requirement holding, secure multi-party computation technology and Sharemind MPC guarantee the confidentiality of private values, except the ones that are explicitly published by all three servers (either to the user or the servers themselves).